November 2025 sent shockwaves through the DeFi lending sector when Moonwell, a protocol running on both Base and Optimism, suffered a devastating exploit. The attacker leveraged a Chainlink oracle malfunction that valued wrapped restaked Ethereum (wrstETH) at an astronomical $5.8 million per token, a price far removed from reality. With this flawed data, the attacker deposited a trivial amount of wrstETH as collateral, then borrowed massive quantities of wrapped staked Ethereum (wstETH), draining Moonwell’s reserves in a series of rapid flash loan transactions. In total, the protocol lost approximately 295 ETH, worth exactly $1 million at the time of the attack.
How Oracles Became DeFi’s Achilles Heel
This event underscores a recurring theme in DeFi lending exploits 2025: protocols remain dangerously exposed to weaknesses in price oracles. Oracles are supposed to be impartial bridges between blockchains and the real world, but when they falter, whether due to bugs, manipulation, or faulty feeds, the results can be catastrophic. In Moonwell’s case, reliance on a single Chainlink feed for wrstETH pricing proved fatal. The attacker capitalized on this vulnerability within a single block using flash loans, instantaneous, collateral-free loans that must be repaid within one transaction, to maximize their haul before any countermeasures could trigger.
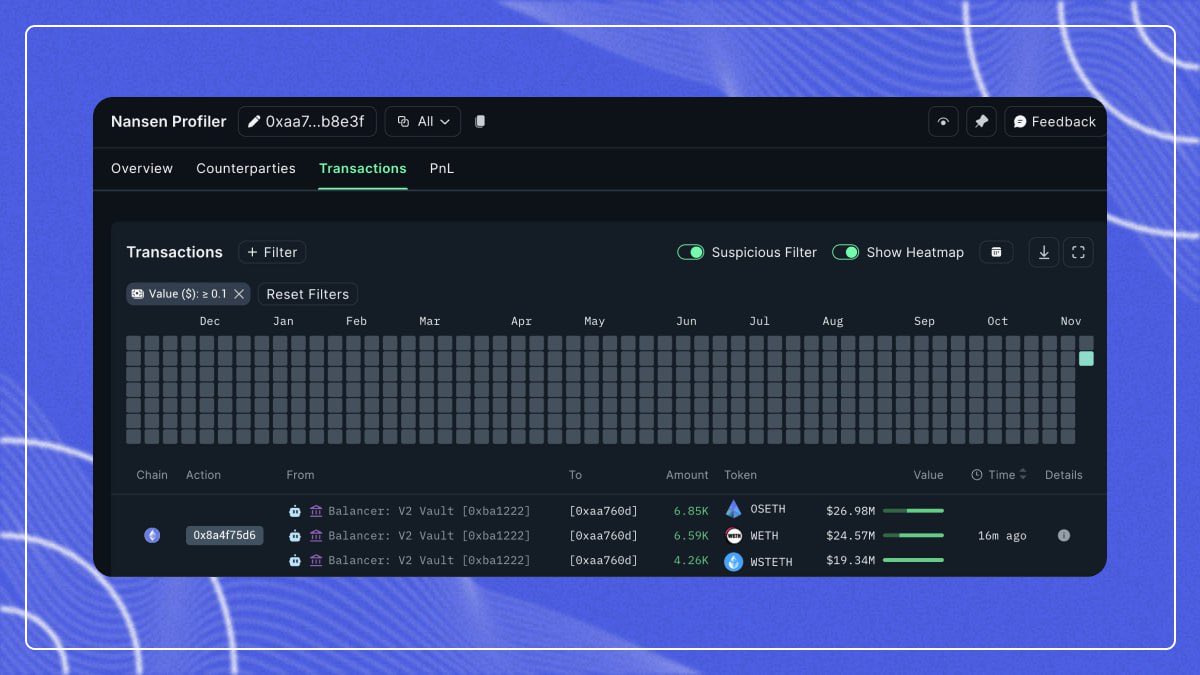
Moonwell is not alone; similar exploits have hit other protocols recently, including Balancer and Stream DeFi. Each incident is different in its technical details but echoes the same refrain: oracle manipulation is among the most lucrative vectors for smart contract vulnerability coverage. For those seeking more technical insight into how these price feed failures cascade into multi-million dollar losses across protocols, see our in-depth analysis here.
The Flash Loan Playbook: Anatomy of an Exploit
The mechanics behind this exploit are instructive for anyone serious about flashloan exploit prevention. Here’s what happened:
- Oracle price error: Chainlink’s wrstETH feed erroneously reported each token at $5.8 million.
- Tiny deposit: The attacker deposited a small amount of wrstETH as collateral, suddenly worth millions due to the glitch.
- Borrows against inflated value: Using this phantom wealth as backing, they borrowed large amounts of wstETH from Moonwell.
- Flash loan cycle: Through multiple rapid iterations within one block (thanks to flash loans), they drained nearly all available funds.
This was not brute force hacking, it was precision exploitation enabled by composability and speed unique to DeFi.
The Path Forward: Multi-Layered Defense Strategies
The Moonwell attack has catalyzed urgent debate around risk mitigation for lending protocols. Here are some actionable strategies gaining traction across security circles:
- Diversified Oracle Sources: Aggregating data from multiple independent oracles makes it much harder for attackers to manipulate prices undetected.
- Price Sanity Checks: By validating incoming price data against recent averages or predefined bounds, protocols can automatically flag and reject outliers like those seen in this exploit.
- TWAPs (Time-Weighted Average Prices): Calculating prices over longer intervals helps neutralize short-term spikes or glitches that might otherwise enable attacks within a single block.
- Circuit Breakers: Automated systems can pause borrowing/lending if abnormal activity or wild price swings are detected, buying time for human intervention before major losses accrue.
- Aggressive Auditing and Bug Bounties: Regular code reviews and incentivized bug hunting help catch vulnerabilities before adversaries do. Community vigilance remains an underutilized asset in DeFi security.
The right combination of these tools can dramatically reduce exposure, not just to oracle-based attacks but also other forms of protocol manipulation seen throughout 2025’s volatile market landscape.
Yet, even with these best practices, the evolving sophistication of attackers means risk can never be eliminated, only managed. The Moonwell exploit is a wake-up call for teams building in DeFi: security is not a one-time box to check but an ongoing process. Protocols that invest in layered defenses and transparent communication with their communities are far more likely to weather these storms.
Insurance and User Protection: A New Standard?
As exploits like Moonwell’s make headlines, the appetite for DeFi insurance for lending protocols is surging. Coverage offerings now go well beyond basic smart contract audits. Leading DeFi insurance providers are rolling out products specifically designed to protect users from oracle failures and flash loan exploits. These policies can reimburse losses if a protocol’s security stack fails, providing peace of mind for both retail users and institutional players.
The market’s response has been swift: protocols that offer built-in insurance or partner with coverage platforms are seeing stronger user retention post-exploit. For investors, this signals a new era where risk-adjusted yield means factoring in not just APY but also the robustness of safety nets.
Checklist: Is Your Protocol Flash Loan-Resistant?
If you’re a developer or project lead in DeFi, use this quick checklist to assess your protocol’s readiness against the next wave of attacks:
Community Vigilance and The Road Ahead
Ultimately, robust code is only part of the equation. The most resilient ecosystems foster active dialogue between developers, auditors, users, and insurance providers. Open-source bug bounty programs and transparent post-mortems transform every exploit into an opportunity to harden the entire sector.
The Moonwell incident will be studied as a case study for years to come, a reminder that composability cuts both ways in DeFi. As we look toward 2026, expect more protocols to double down on multi-layered defenses and integrate risk transfer mechanisms at their core.
For those seeking a deeper dive into the technical mechanics behind these attacks, and practical mitigation strategies, explore our detailed research on oracle price feed vulnerabilities.