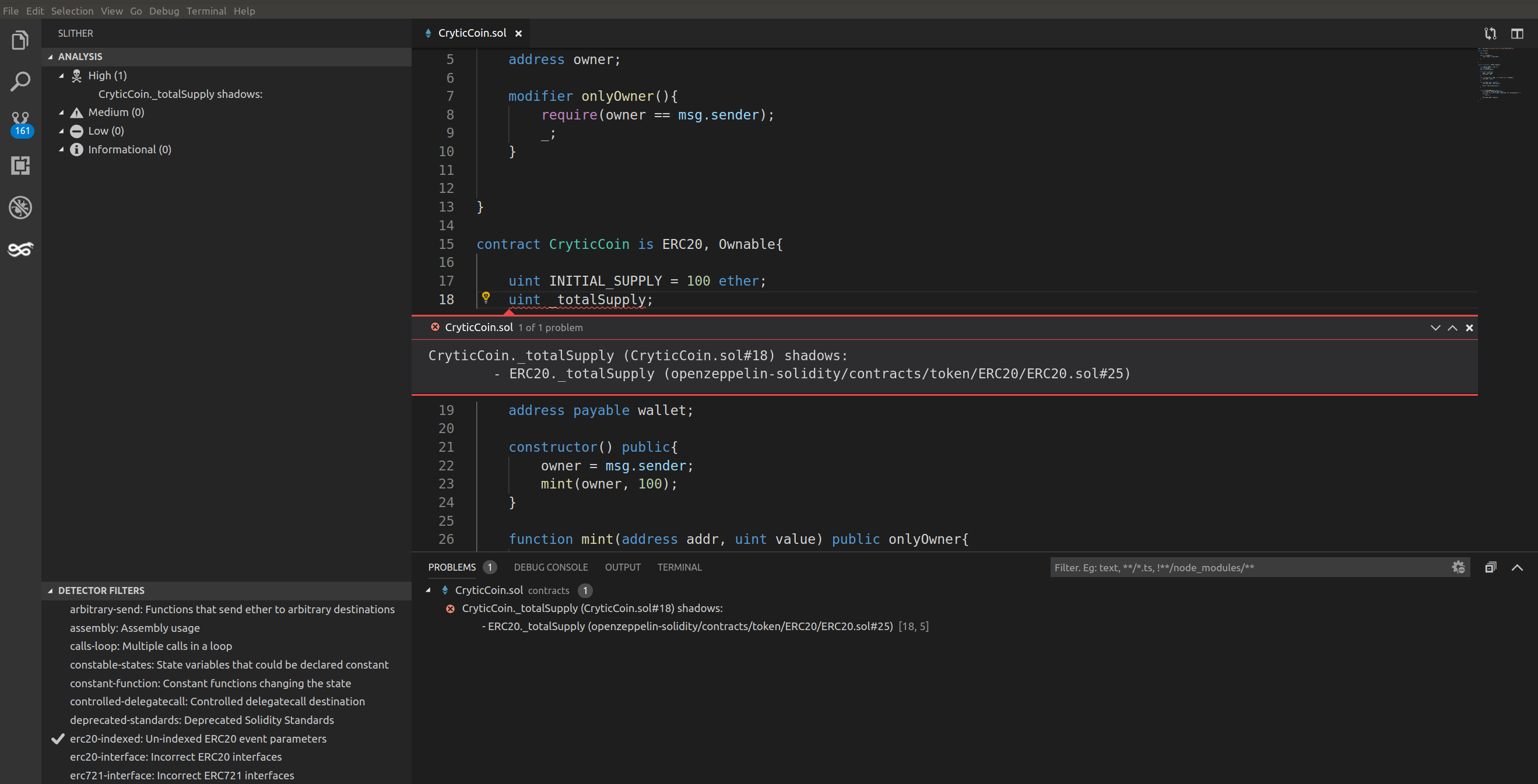
Access control flaws are quietly responsible for some of the largest financial catastrophes in decentralized finance. In 2025 alone, these vulnerabilities accounted for a staggering $1.46 billion in losses across just eight incidents in Q1, making up over 70% of all DeFi funds lost during that period. The lesson is clear: DeFi access control flaws are not just bugs, they are billion-dollar liabilities.
What Are Access Control Flaws in DeFi?
At their core, access control flaws occur when smart contracts fail to restrict who can execute sensitive functions. In traditional finance, think of this as giving a bank teller the keys to the vault with no oversight. In DeFi, this can mean anyone, not just the protocol’s team or a multisig, can mint tokens, drain liquidity pools, or upgrade contracts. The consequences are often catastrophic, as seen in the Bybit exploit of February 2025, which resulted in a record-breaking $1.4 billion loss.
Common types of access control vulnerabilities include:
Common Access Control Vulnerabilities in DeFi
-
Unrestricted Function Access: Failing to restrict access to critical smart contract functions allows unauthorized users to execute sensitive operations, as seen in several major DeFi exploits.
-
Improper Role Assignments: Misconfigured or overly broad roles grant excessive permissions to users or addresses, increasing the risk of privilege escalation and abuse.
-

Compromised Private Keys: Unauthorized access to private keys, often due to poor key management, can give attackers full control over smart contracts and funds, as demonstrated in high-profile incidents.
-

Lack of Multi-Signature Controls: Absence of multi-signature requirements for critical actions means a single compromised account can lead to total loss, rather than requiring consensus among multiple trusted parties.
-
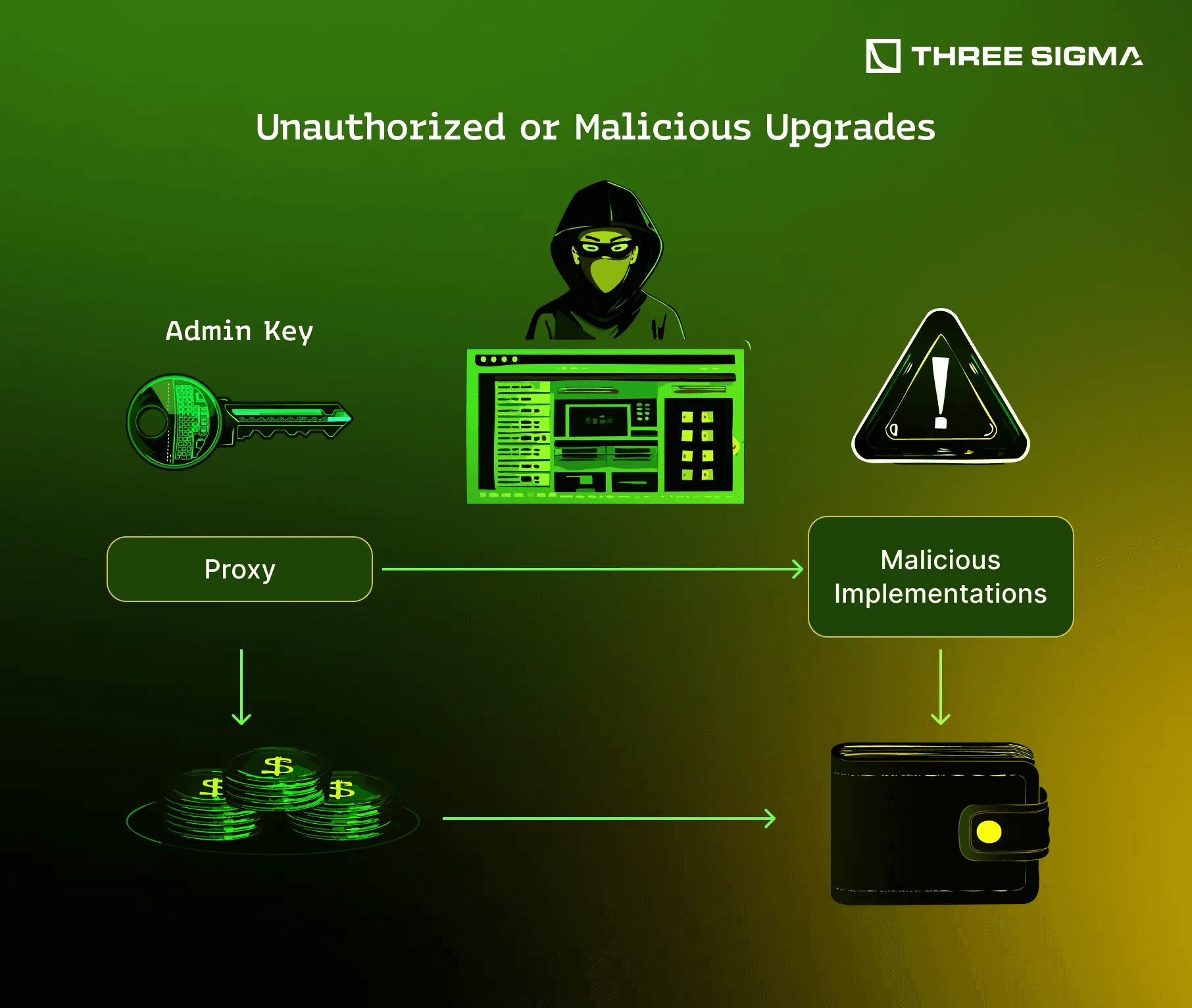
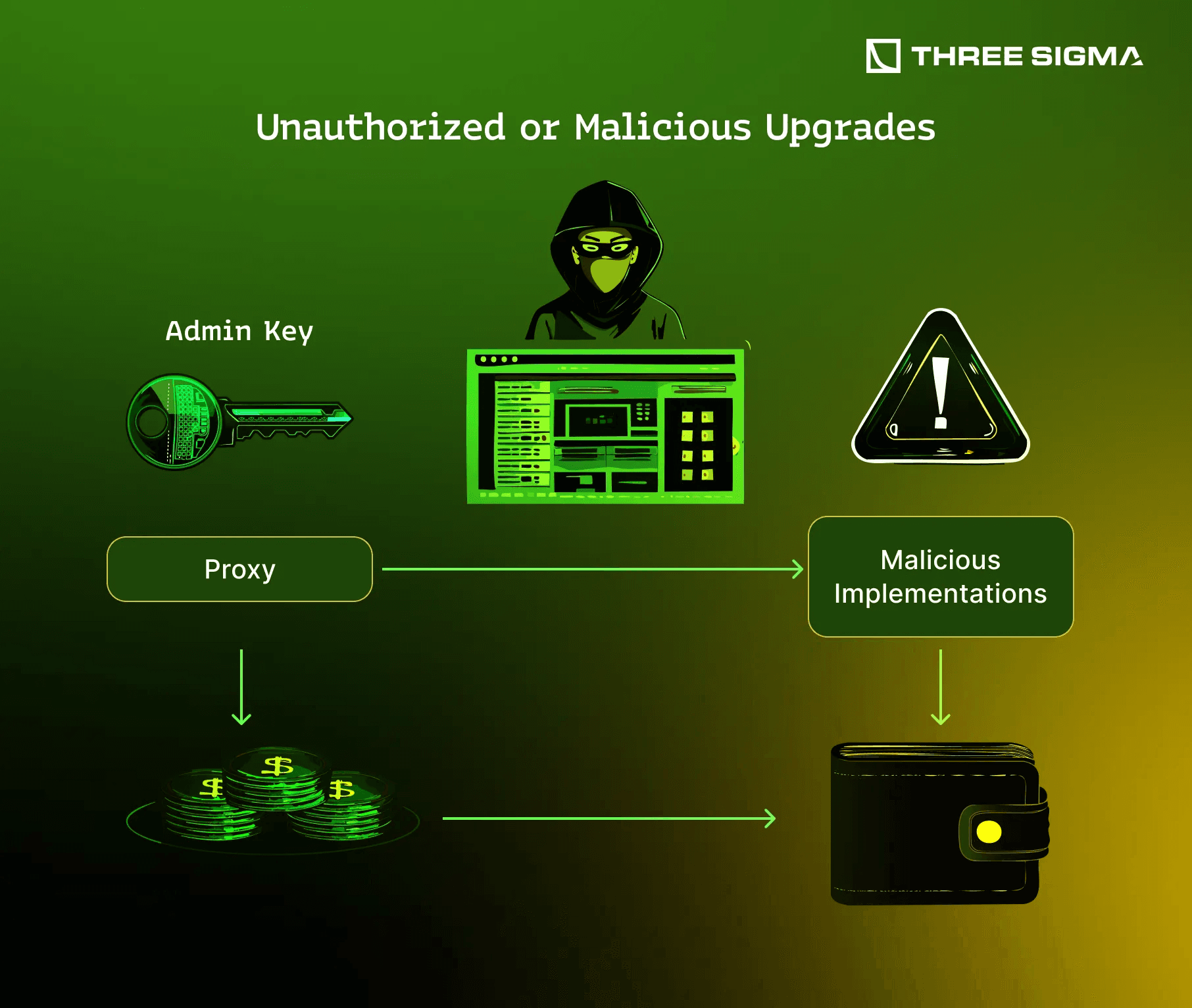
Insecure Upgrade Mechanisms: Poorly protected upgrade functions allow attackers to modify contract logic or redirect funds, as in the 2018 Bancor Network hack and other upgrade-related exploits.
DeFi Exploit Case Studies: How Permission Checks Fail
Let’s look at how these flaws play out in the real world. The Poly Network hack of August 2021 is a textbook example. Attackers exploited poorly implemented permission checks to transfer over $610 million in digital assets to their own wallets. More recently, the Bybit breach stemmed from an access control oversight that allowed unauthorized contract upgrades and fund transfers.
Even smaller projects aren’t immune. Infini lost $49.5 million due to a single access control misconfiguration. These incidents share a common thread: a critical smart contract permission check was missing, misapplied, or bypassed entirely.
The Anatomy of a Smart Contract Access Control Flaw
So, how do these vulnerabilities actually occur? Here are the most frequent culprits:
- Unrestricted Function Access: Functions like
withdraw(),upgrade(), ormint()are left open to anyone, rather than being limited to authorized roles. - Improper Role Assignments: Roles with excessive privileges are assigned to addresses that shouldn’t have them, or roles are never revoked after use.
- Compromised Private Keys: Even well-designed contracts can be compromised if private keys controlling admin functions are stolen or leaked.
The result? Attackers can drain funds, disrupt governance, or take over protocols in a matter of minutes. With the rapid composability of DeFi, one exploit can cascade across multiple platforms, amplifying the damage.
The Stakes: Why Access Control Matters More Than Ever
The scale of recent incidents cannot be overstated. According to the Q3 2025 de. fi Rekt Report, access control weaknesses caused $188.7 million in losses across 13 separate incidents. This is not an isolated trend, it’s a persistent threat that continues to evolve as DeFi grows more complex and interconnected.
If you’re a developer, investor, or user in the DeFi space, understanding smart contract permission checks is no longer optional. It’s essential for risk mitigation and long-term survival in an industry where a single overlooked line of code can cost millions.
For those navigating this landscape, the difference between robust access controls and a catastrophic exploit often comes down to a handful of crucial technical decisions. The most effective teams treat permission management not as an afterthought, but as a core pillar of protocol design. When ignored, even the most innovative DeFi projects can be wiped out overnight.
Proven Strategies for Smart Contract Risk Mitigation
Fortunately, the industry is developing a toolkit of best practices to combat these threats. Here are some of the most impactful approaches:
Essential Strategies to Mitigate DeFi Access Control Flaws
-
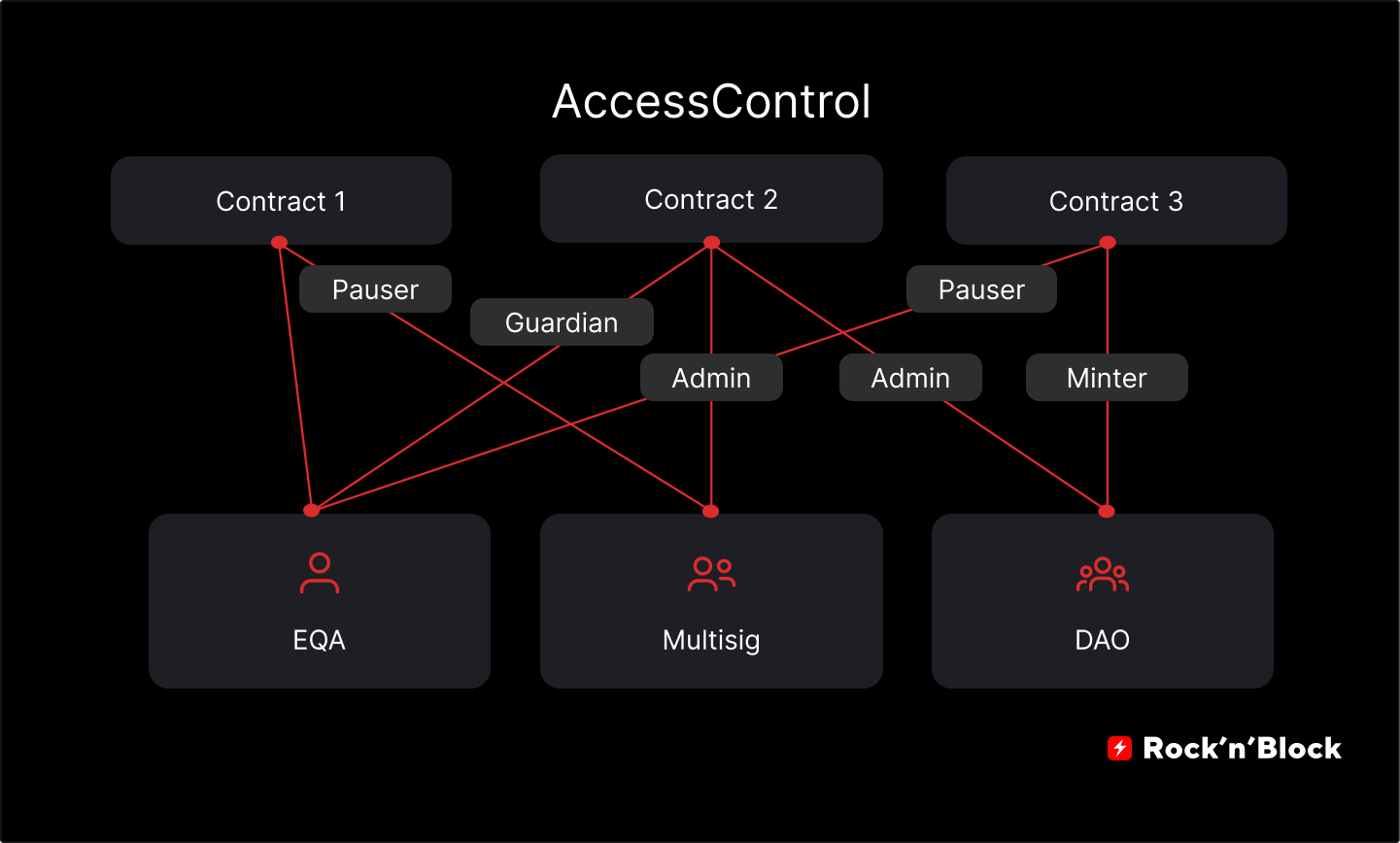
Implement Role-Based Access Control (RBAC): Use frameworks like OpenZeppelin AccessControl to define precise roles and permissions, ensuring only authorized accounts can execute sensitive functions.
-

Conduct Regular Security Audits: Engage reputable firms such as Trail of Bits, ConsenSys Diligence, or Halborn for comprehensive code reviews to uncover and address access control vulnerabilities.
-
Adopt Multi-Signature Wallets: Use solutions like Gnosis Safe to require multiple approvals for critical transactions, reducing the risk of a single compromised key leading to catastrophic loss.
-

Secure Private Key Management: Store private keys in Hardware Security Modules (HSMs) or use trusted custody services such as Fireblocks to prevent unauthorized access and mitigate risks from key leaks.
-

Monitor and Respond to On-Chain Activity: Employ platforms such as Forta or Chainalysis for real-time threat detection and incident response to suspicious contract interactions.
-
Follow Established Security Standards: Adhere to best practices outlined in the ConsenSys Smart Contract Best Practices guide to ensure robust access control implementations.
Role-Based Access Control (RBAC) is foundational. By defining precise roles, admin, operator, user, and restricting sensitive functions accordingly, protocols can limit the damage from compromised accounts or insider threats. OpenZeppelin’s AccessControl library has become a gold standard for implementing RBAC in Ethereum-based contracts.
Security audits are another non-negotiable step. Frequent code reviews by specialized firms can catch subtle permission errors before they go live. Static analysis tools like AChecker are increasingly used to scan for misconfigurations and missing access checks at scale (asemghaleb.com). However, audits are only as good as their scope, continuous monitoring post-deployment is just as critical.
Private key management remains a linchpin in DeFi security. Even perfectly coded contracts can be undermined if admin keys aren’t protected with hardware wallets or multi-signature schemes. The push towards decentralized governance and on-chain role assignments is gaining traction precisely because it reduces reliance on single points of failure.
DeFi Insurance: A Safety Net for Access Control Failures?
No matter how diligent a project is, zero risk doesn’t exist in DeFi. This reality has spurred growth in DeFi insurance solutions, specifically designed to cover losses from smart contract exploits, including those caused by access control flaws. Leading platforms now offer policies that reimburse users if funds are lost due to unauthorized contract actions or governance attacks.
If you’re considering insurance for your digital assets, look for providers with clear coverage on smart contract permission breaches and transparent claims processes. Remember: insurance should complement strong technical defenses, not replace them.
Staying Ahead: Education and Community Vigilance
The best defense is an informed community. Developers should prioritize ongoing education about evolving threat vectors; users should demand transparency around protocol upgrades and admin powers; investors must scrutinize audit reports before committing capital.
Have you ever suffered losses due to a DeFi access control exploit?
Access control flaws have led to over $1.46 billion in DeFi losses in Q1 2025 alone. We’re curious about your personal experience—have you been affected by these types of vulnerabilities?
If you want to dive deeper into real-world cases and actionable solutions, download the Top 100 DeFi Hacks Report 2025 (Halborn). For more technical guidance on secure permission checks in smart contracts, resources like QuillAudits’ guide on access control vulnerabilities provide excellent starting points.
Key Takeaways for Developers and Users
- Treat every permission check as mission-critical: One overlooked function can cost millions.
- Avoid single points of failure: Use multisig wallets and decentralized governance wherever possible.
- Pursue layered defenses: Combine RBAC with rigorous audits and real-time monitoring tools.
- Consider DeFi insurance: Especially if you’re holding significant value in unaudited or experimental protocols.
The stakes have never been higher, but neither has the potential for innovation when security is prioritized from day one. As always: protect first, grow second.