EVM proxy contracts are the backbone of upgradeable DeFi protocols, but their flexibility comes at a steep security price. In 2024 alone, attackers have exploited weak proxy patterns and cross-chain synchronization flaws to drain millions from leading platforms. If you’re building or investing in DeFi, understanding these risks isn’t optional, it’s essential for survival.

Why Proxy Contract Vulnerabilities Are DeFi’s Weakest Link
Proxy contracts separate logic from storage, enabling seamless upgrades and rapid iteration. But this same architecture introduces new attack surfaces that traditional smart contracts never faced. The two most critical exploit trends right now are:
Top EVM Proxy Exploit Trends & Protection Tactics
-
Unauthorized Proxy Implementation Upgrades: Attackers exploit poorly secured or unprotected proxy admin functions to upgrade contract logic to malicious implementations, often resulting in total asset loss. Protection Strategy: Enforce strict access controls (e.g., multi-signature wallets like Gnosis Safe, timelocks) on upgrade functions and conduct regular audits of proxy admin permissions to prevent unauthorized changes.
-
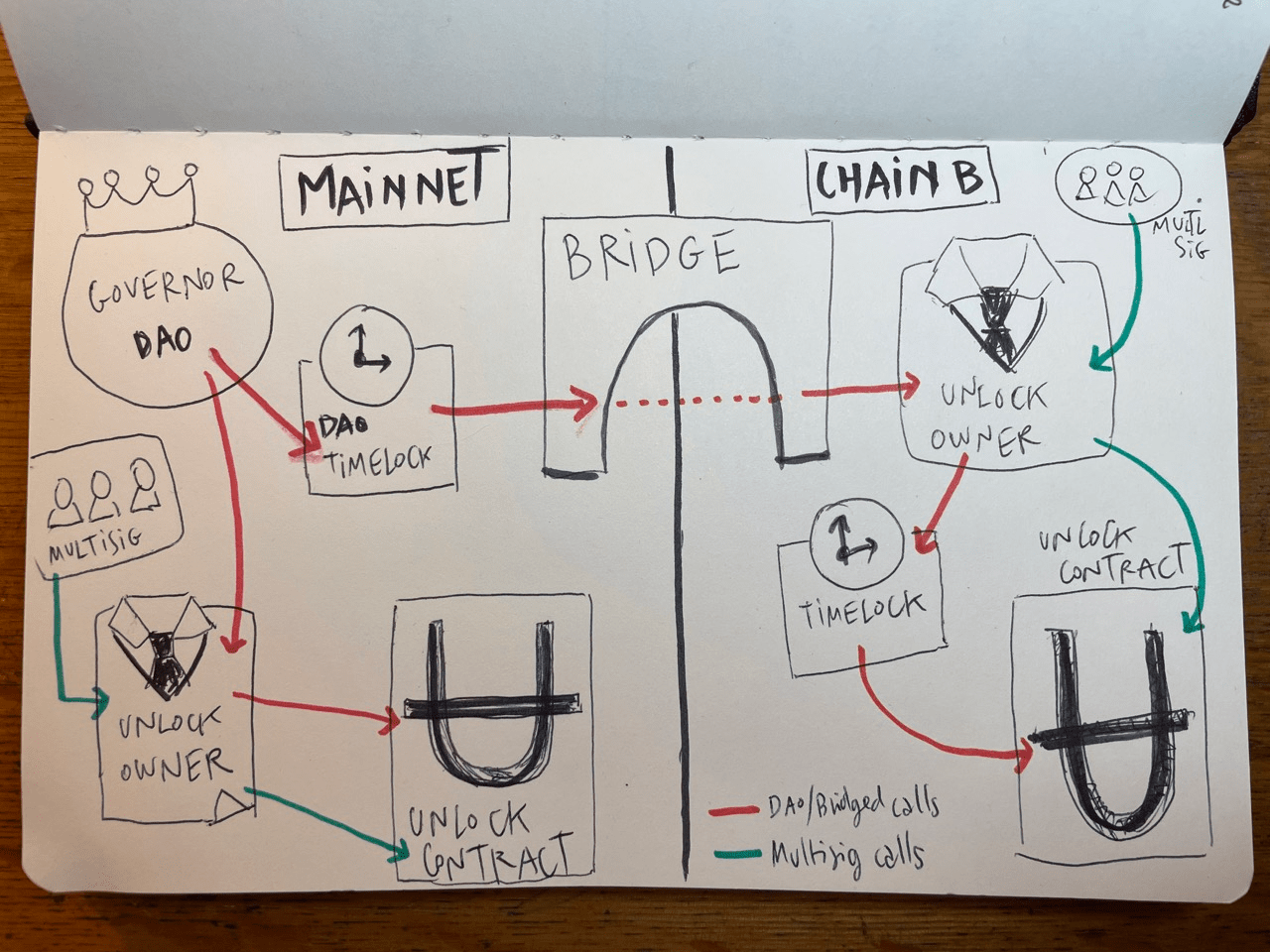
Cross-Chain Proxy Manipulation Attacks: Exploits leverage inconsistencies or delays in cross-chain bridge validation and proxy contract state synchronization to redirect or drain assets across networks. Protection Strategy: Employ robust cross-chain message verification (e.g., Chainlink CCIP, consensus-based relayers), and implement real-time monitoring for anomalous proxy upgrade or call patterns to detect and halt attacks early.
- Unauthorized Proxy Implementation Upgrades: Attackers exploit poorly secured proxy admin functions to swap in malicious logic, often resulting in catastrophic asset loss. This is not hypothetical, multiple high-profile protocols have been wiped out by a single compromised admin key or unprotected upgrade function.
- Cross-Chain Proxy Manipulation Attacks: As protocols chase liquidity across chains, attackers are leveraging inconsistencies in bridge validation and proxy state syncs. By exploiting these gaps, they can redirect or drain assets across networks before anyone notices.
Case Study: How Attackers Hijack Proxy Upgrades
The most devastating attacks in 2024 have centered around unauthorized proxy implementation upgrades. Here’s how it typically unfolds:
- The attacker identifies a protocol where proxy admin functions (like
upgradeTo()) are insufficiently protected, sometimes even left open to any caller. - They call the upgrade function, pointing the proxy to their own malicious contract implementation. Instantly, they gain control over funds or critical protocol logic.
- In several recent cases, this led to total asset loss within minutes, no time for community intervention or governance rollback.
Protection Strategy: The only way to reliably defend against this is to combine strict access controls with rigorous operational discipline. Industry best practices include:
- Multi-signature wallets: Require multiple independent approvals before any proxy upgrade can occur.
- Timelocks: Add a delay to upgrades, giving the community time to react to suspicious proposals.
- Regular audits: Continuously review proxy admin permissions and monitor for unauthorized changes. For more on these best practices, see the latest DeFi security guidance.
Cross-Chain Proxy Manipulation: The New Frontier of DeFi Exploits
With over $21 million lost in arbitrary external call exploits and $37 million in governance-based attacks in just one year, cross-chain vulnerabilities are now at the center of DeFi’s risk landscape. When protocols rely on cross-chain bridges, delays or inconsistencies in message verification can be fatal. Attackers exploit these windows to manipulate proxy states or redirect assets before the bridge or protocol can react.
Protection Strategy:
- Robust cross-chain message verification: Leverage proven solutions like Chainlink CCIP or consensus-based relayers to ensure only validated messages trigger proxy upgrades or sensitive calls. For a deep dive into bridge security, check out this analysis on bridge vulnerabilities.
- Real-time monitoring: Deploy automated systems that flag anomalous proxy upgrade patterns or suspicious cross-chain calls. Rapid detection is critical for stopping attacks before assets are drained.
Actionable Checklist for Developers and Investors
These exploit patterns aren’t theoretical, they’re shaping the DeFi landscape right now. Protocols that fail to lock down proxy upgrades or overlook cross-chain validation are prime targets, and the numbers speak for themselves: over $58 million lost to these two attack vectors in the past year alone. The sophistication of attackers is rising, and so is the complexity of the DeFi stack. If you’re not actively defending against these threats, you’re betting your treasury on luck.
Building Resilience: Best Practices for Proxy Contract Security
Effective defense starts with a layered approach to security. Here’s what separates resilient protocols from those destined for the next exploit headline:
- Strict Role Separation: Never let a single entity control proxy admin keys. Use dedicated, isolated accounts for upgrade permissions, and rotate these regularly.
- Transparent Governance: Publish all proxy upgrade proposals and require community review before execution, timelocks give users vital reaction time.
- Automated Alerting: Integrate on-chain monitoring tools that instantly flag unauthorized upgrade attempts or unexpected cross-chain calls.
- Continuous Testing: Employ fuzzing, formal verification, and rigorous scenario-based audits to uncover edge-case vulnerabilities before attackers do.
For cross-chain protocols, this diligence extends to every bridge integration and message relay. Attackers are probing for the smallest window of inconsistency between chains, one missed sync or unchecked message can open the floodgates.
What Investors Need to Watch
If you’re allocating capital to DeFi protocols, demand transparency around proxy upgrade processes and cross-chain validation mechanisms. Ask hard questions:
- Who controls the proxy admin keys?
- Are upgrades gated by multi-sig and timelock contracts?
- Is there independent monitoring of bridge activity and proxy state changes?
The protocols that can answer these questions confidently, and demonstrate real controls in place, are far less likely to end up as cautionary tales.
Key Takeaways for DeFi Stakeholders
Key Proxy Contract Exploit Trends & Protection Strategies
-
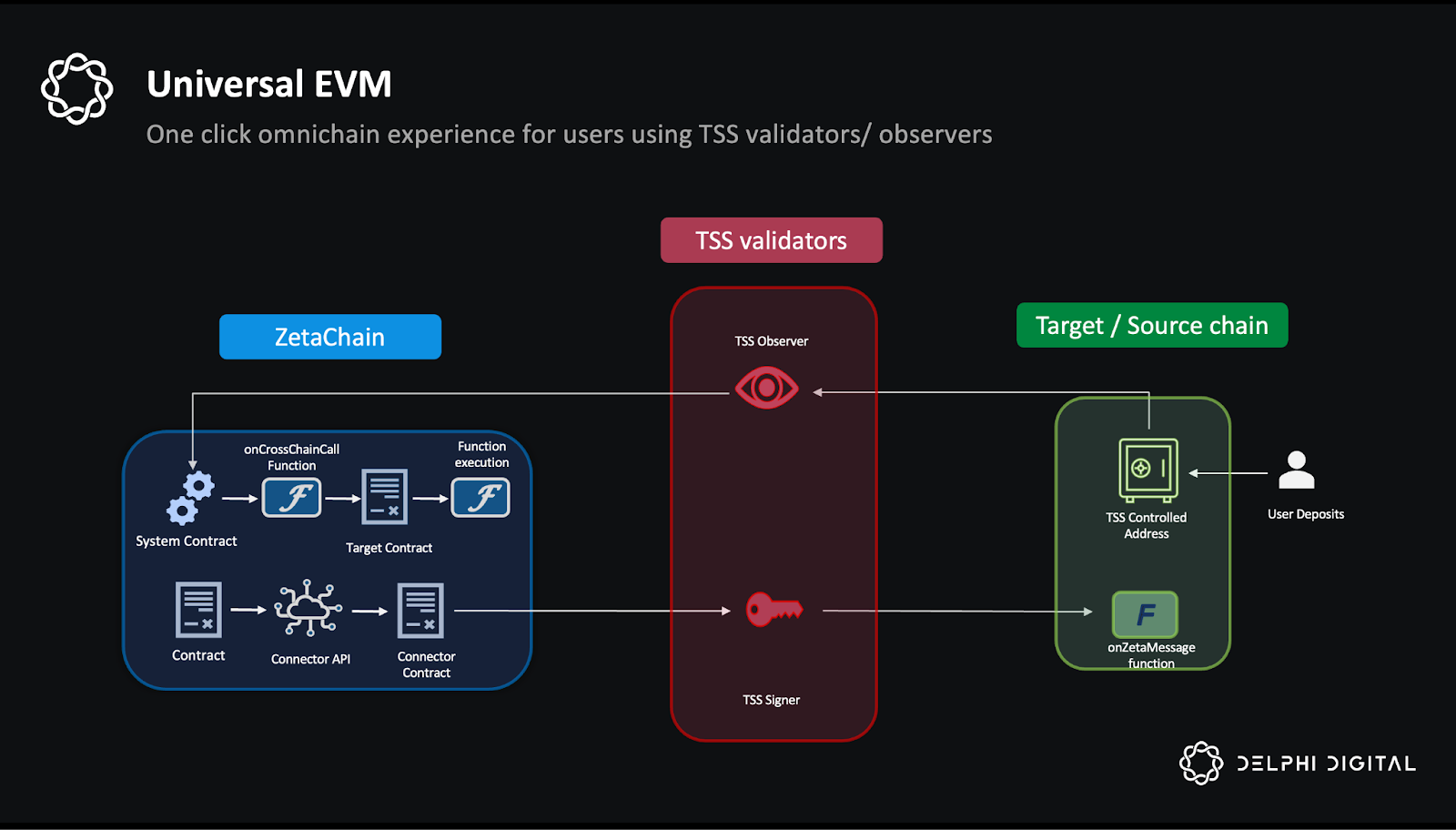
Unauthorized Proxy Implementation Upgrades: Attackers exploit poorly secured or unprotected proxy admin functions to upgrade contract logic to malicious implementations, often resulting in total asset loss. Protection Strategy: Enforce strict access controls (e.g., multi-signature wallets, timelocks) on upgrade functions and conduct regular audits of proxy admin permissions.
-

Cross-Chain Proxy Manipulation Attacks: Exploits leverage inconsistencies or delays in cross-chain bridge validation and proxy contract state synchronization to redirect or drain assets across networks. Protection Strategy: Employ robust cross-chain message verification (e.g., Chainlink CCIP, consensus-based relayers), and implement real-time monitoring for anomalous proxy upgrade or call patterns.
The bottom line: EVM proxy contract vulnerability is not a niche concern but a systemic risk that demands ongoing vigilance. Developers must treat upgrade paths as critical infrastructure, not afterthoughts. Investors need to scrutinize governance and cross-chain security like they would any other core protocol feature.
This is an arms race, and only those who stay ahead of evolving exploit trends will keep their assets secure in an increasingly adversarial DeFi ecosystem.